KB ID 0000533
Problem
If you have a server or host that you want to be publicly addressable and only have one public IP address then port forwarding is what you require.
Solution
Assumptions
1. You have a public IP on the outside of your Router.
2. You are performing NAT from your internal range of IP address to your External IP address.
To Make Sure
1. Run the following command:
You should see a line like,
2. That means NAT all traffic that access-list 101 applies to, to Dialer0 (this is an ADSL router and that’s it’s outside interface). To see what traffic is in access-list 101 is issue the following command:
You should see a line like,
3. This means permit (apply this ACL) to all traffic from 10.10.0.0/16 to anywhere. So its set to NAT all traffic from the inside network to the outside network.
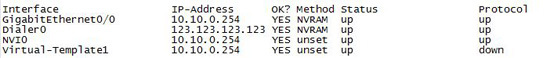
4. Finally to see what IP is on your Dialer0 issue the following command:
You should see something like this
Now we know all traffic from 10.10.0.0/24 (All inside traffic) will be NAT translated to 123.123.123.123
Set up Port Forwarding
In this case Ill port forward TCP Port 443 (HTTPS) and TCP Port 25 (SMTP) to an internal Server (10.10.0.1).
1. First set up the static NAT translations.
PetesRouter#ip nat inside source static tcp 10.10.0.1 443 123.123.123.123 443 extendable PetesRouter#ip nat inside source static tcp 10.10.0.1 25 123.123.123.123 extendable OR If you are running with a Public DHCP address PetesRouter#ip nat inside source static tcp 10.10.0.1 443 interface Dialer0 443 PetesRouter#ip nat inside source static tcp 10.10.0.1 25 interface Dialer0 25
2. Second stop that traffic being NATTED with everything else.
PetesRouter#access-list 101 deny tcp host 10.10.0.1 eq 443 any
PetesRouter#access-list 101 deny tcp host 10.10.0.1 eq 25 any3. Save the changes with “copy run start”, then press enter to access the default name of startup-config:
PetesRouter#copy run start
Destination filename [startup-config]?
Building configuration...
[OK]
PetesRouter#Setup port forwarding and restrict it to an IP or network
For things like HTTPS and SMTP you might want them accessible from anywhere but you might want to lock down access for something like RDP, (TCP port 3389) if that’s the case then you need to do the following.
1. Create a new ACL that allows traffic from you but denies it from everyone else (remember to put an allow a permit at the end).
PetesRouter#access-list 199 permit tcp host 234.234.234.234 host 123.123.123.123 eq 3389
PetesRouter#access-list 199 deny tcp any host 123.123.123.123 eq 3389
PetesRouter#access-list 199 permit ip any anyNote: To allow a network substitute the first line for,
Note: Cisco Routers use inverted masks, so 234.234.234.232 0.0.0.7 is 234.234.234.232 255.255.255.248 (or/29)
2. Then (as in the example above) create the static NAT translation.
3. Then (as in the example above) exempt this traffic from the default NAT ACL.
4. Finally apply the ACL you created inbound on the Dialer0 interface.
PetesRouter#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
PetesRouter(config)#interface Dialer0
PetesRouter(config-if)#ip access-group 199 in
PetesRouter(config-if)#exit
PetesRouter#5. Save the changes with “copy run start”, then press enter to access the default name of startup-config:
PetesRouter#copy run start
Destination filename [startup-config]?
Building configuration...
[OK]
PetesRouter#Related Articles, References, Credits, or External Links
Cisco PIX / ASA Port Forwarding